As technology continues to advance, the threat of cyber attacks on businesses becomes increasingly prominent. In order to protect your business, it is important to understand the most common cyber security threats and take the necessary measures to prevent them. In this article, we will discuss the top 8 cyber security threats that businesses face in 2023.
Table of Contents
8 Cyber Security Threats to Businesses in 2023
Ransomware Cyber Security
Ransomware is a type of malware that encrypts a business’s data and demands a ransom in exchange for the decryption key. This type of attack can be devastating to a business, as it can result in the loss of important data and a significant amount of downtime. To prevent a ransomware attack, businesses should regularly backup their data and ensure that their systems are fully updated with the latest security patches.

Phishing Attacks Cyber Security
Phishing attacks are a common type of cyber attack that can be used to steal sensitive information such as passwords and credit card numbers. These attacks often take the form of emails or websites that look like they are from a reputable source, but in reality, they are designed to trick the user into entering their personal information. To prevent phishing attacks, businesses should educate their employees on the dangers of these types of attacks and ensure that they are aware of the signs of a phishing attempt.

Malware Cyber Security
Cyber Security Malware is a type of software that is designed to cause harm to a computer system. This type of software can come in the form of viruses, worms, Trojans, and spyware. To prevent malware attacks, businesses should ensure that their systems are fully updated with the latest security patches and run regular malware scans. Additionally, businesses should avoid downloading software from untrusted sources and should be wary of opening email attachments from unknown senders.

Man-in-the-Middle Attacks Cyber Security
Man-in-the-middle attacks occur when a hacker intercepts communication between two parties, allowing them to steal sensitive information such as passwords and credit card numbers. To prevent man-in-the-middle attacks, businesses should ensure that their websites are properly encrypted and that they are using secure protocols such as SSL or TLS.

SQL Injection Attacks Cyber Security
SQL injection attacks occur when a hacker injects malicious code into a website’s database, allowing them to steal sensitive information or manipulate the website’s data. To prevent SQL injection attacks, businesses should ensure that their websites are fully updated with the latest security patches and that they are using proper security measures such as input validation and sanitization.

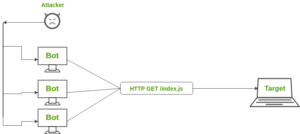
Distributed Denial of Service (DDoS) Attacks
DDoS attacks occur when a large number of computers are used to flood a website with traffic, making it impossible for the website to respond to legitimate requests. To prevent DDoS attacks, businesses should ensure that their websites are hosted on servers with adequate resources and that they have the proper measures in place to mitigate the effects of a DDoS attack.
Insider Threats Cyber Security
Insider threats occur when an employee or contractor intentionally or unintentionally causes harm to a business. This type of threat can take many forms, including theft of sensitive information, unauthorized access to systems, and the introduction of malware into the business’s network. To prevent insider threats, businesses should implement strict security policies and monitor employee activity to ensure that their systems and data remain secure.

Unpatched Software Vulnerabilities Cyber Security
Unpatched software vulnerabilities are security weaknesses or flaws in software that have been discovered but have not yet been fixed by the software vendor. These vulnerabilities can be exploited by attackers to gain unauthorized access to systems, steal sensitive data, or cause other harm. It is important for organizations to keep their software up to date and patch vulnerabilities as soon as possible to reduce the risk of attack.

In the end, I would suggest the best way to deal with cyber security threats is to always educate and train your employees.
Train your employees
Data security is as powerful as employee knowledge of current security best practices.
Employee Training: recognizes social engineering scams such as phishing and fake forms and links;
Familiarize yourself with the privacy regulations that affect the industry;
Improve password hygiene;
Know what to do if they click on a malware link or endanger your organization’s data or network;
Understand how data security is the first line of defence against hackers.Read More IELTS Coaching in Chandigarh Sector 32 and Sector 34
Develop a cyber security strategy
Developing a comprehensive cybersecurity strategy can be a complex task, but it is important to keep in mind that it should be tailored to the specific needs and goals of your organization. Here are some general steps you can follow to develop a cybersecurity strategy:
- Assess your organization’s current security posture: This step involves evaluating your current security systems, processes, and practices to identify any gaps or vulnerabilities. You should also consider any legal or regulatory requirements that may apply to your organization.
- Identify your critical assets: Determine what assets are most critical to the operation of your organization and prioritize the protection of those assets. This may include sensitive data, systems, networks, or infrastructure.
- Develop a risk management plan: Evaluate the risks to your critical assets and prioritize the risks that need to be addressed first. Consider the likelihood and impact of each risk, and develop a plan to mitigate or transfer those risks.
- Define security policies and standards: Develop policies and standards that outline the security requirements and expectations for employees, contractors, and other stakeholders. This may include policies on password management, data security, and incident response.
- Implement technical controls: Implement technical controls, such as firewalls, intrusion detection and prevention systems, and encryption, to protect your critical assets. Consider using a multi-layer approach that combines multiple technical controls for maximum protection.
- Create an incident response plan: Develop a plan that outlines the steps to be taken in the event of a security breach. This plan should include clear roles and responsibilities and should be regularly tested and updated.
- Train and educate employees: Ensure that employees are trained and aware of the importance of cybersecurity and the role they play in protecting your organization’s assets. Regular training and awareness programs can help reduce the risk of a successful cyber attack.
You Can Also Read About: 8 Best Holi Events in Chandigarh









